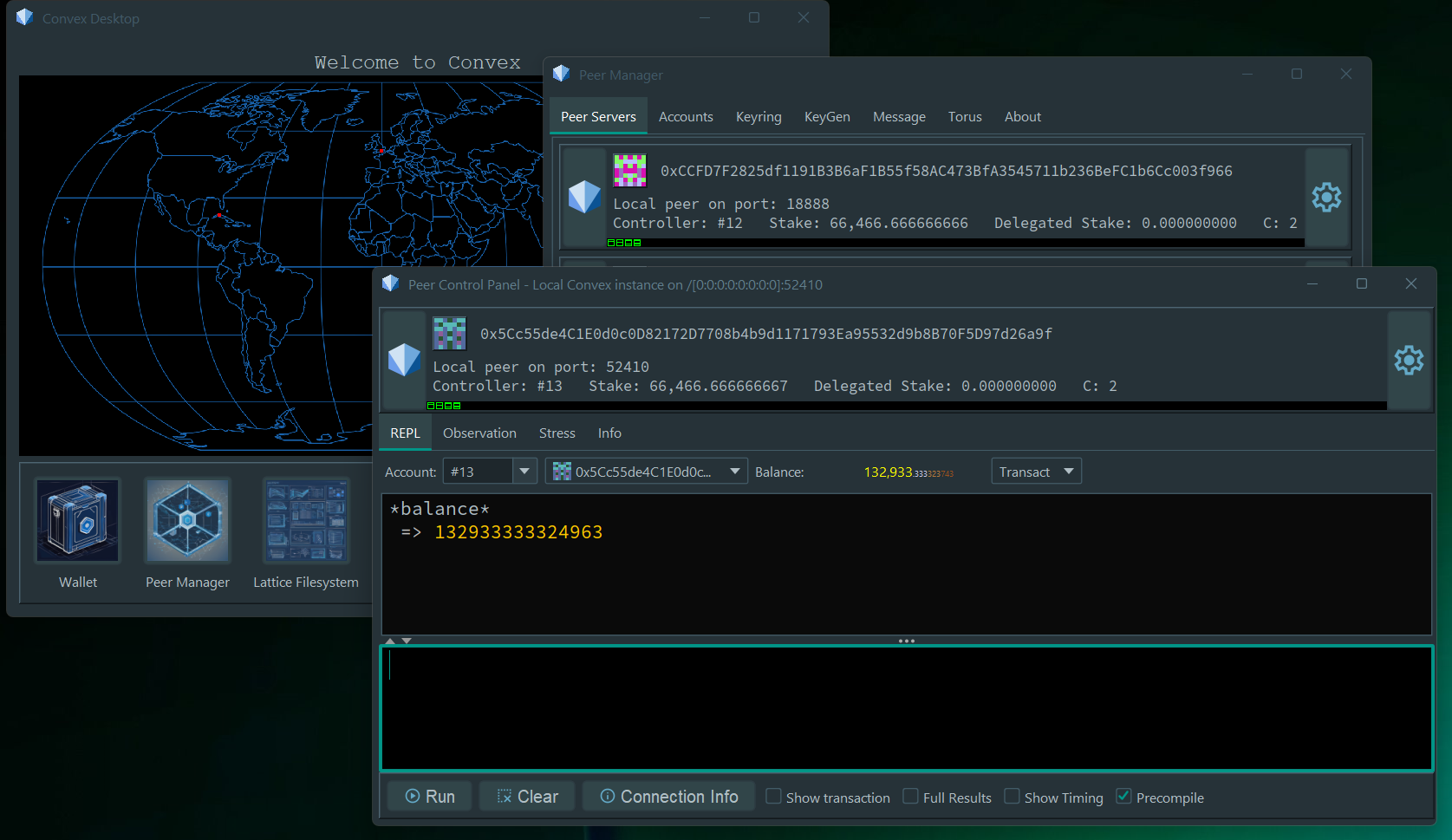
Convex Desktop
Convex Desktop is a GUI tool for interacting with Convex. Designed for developers and power users, it puts all the capabilities of Convex at your fingertips.
Installation
Convex Desktop requires:
- A recent version of Java (21+, Java 25 recommended)
- A GUI based operating system (e.g. Windows, Linux or MacOS)
- A copy of the
convex.jarexecutable jar file
Java is available from multiple providers, we recommend:
Snapshots of the convex.jar file are currently available here: Convex Snapshots
Running Convex Desktop
If Java is configured to run by default for .jar files in your OS, you should be able to run Convex Desktop simply by double-clicking on the convex.jar file which will run Convex Desktop as an executable. On some systems, you may need to grant permissions to run a downloaded executable file.
Alternatively, to run Convex Desktop, you can run the following command from the command prompt, script or GUI shortcut:
java -jar convex.jar desktop
Introduction for non-crypto Developers
Convex Desktop
- Create Convex accounts and Peers via a graphical user interface (GUI) for operating networks
- Allows developers to generate test networks and secure crypto keys prior to production use
- Prepare and test transactions before committing to execution or paying fees
- Manage a wallet for storing keys and account balances
- In production, earn fees for staking and operating Peers
- Use for global scale payments and gaming
Getting Started
- Download the latest convex.jar from Convex Snapshots
- Learn Convex Lisp for more advanced functions
Step 1a: Hacker Tools KeyGen
- Click Generate – 12 words appear in seed Phrase
- Enter Passphrase (lower case)
- Record both somewhere safe. DON’T LOSE
- Key Derivation defaults to
m/44/864/0/0/0(the SLIP-10 standard for Convex). You can change this, but if you do, make sure that you SAFELY record this too. - Copy Private Ed25519 seed somewhere safe. DON’T SHARE. This is also known as Private Key
- Copy Ed25519 Public Key. Can be shared
- Check out your identicon. It will be useful later to recognise your key.
- Normalise mnemonic sets lower case
- Click Add to keyring
Step 1b: Hacker Tools Load Keystore
- Icon for swift recognition
- Public key to share
- Source = location of keystore
- Lock for extra security, keep separate from other keys and passphrases.